How does River protect
your funds?
your funds?
How does River protect
your account?
your account?
Unparalleled transparency with Proof of Reserves

Verify your bitcoin holdings
River publishes monthly Proof of Reserves so you can verify that we hold the bitcoin we say we do. We do not lend out your bitcoin.
River has the highest security standards

Multisig cold storage
100% of client bitcoin deposits are kept in cold storage after being purchased, meaning they are isolated from the Internet.
Custody not built on third-parties
River has full control over its bitcoin custody infrastructure to minimize dependencies on third parties.

FDIC insured cash up to $250,000
US dollars deposited on River are held in an interest-bearing account at Lead Bank, which provides FDIC insurance.¹

SOC II compliance
River has strict data controls across its systems and is SOC II compliant.
Account security you can't get elsewhere
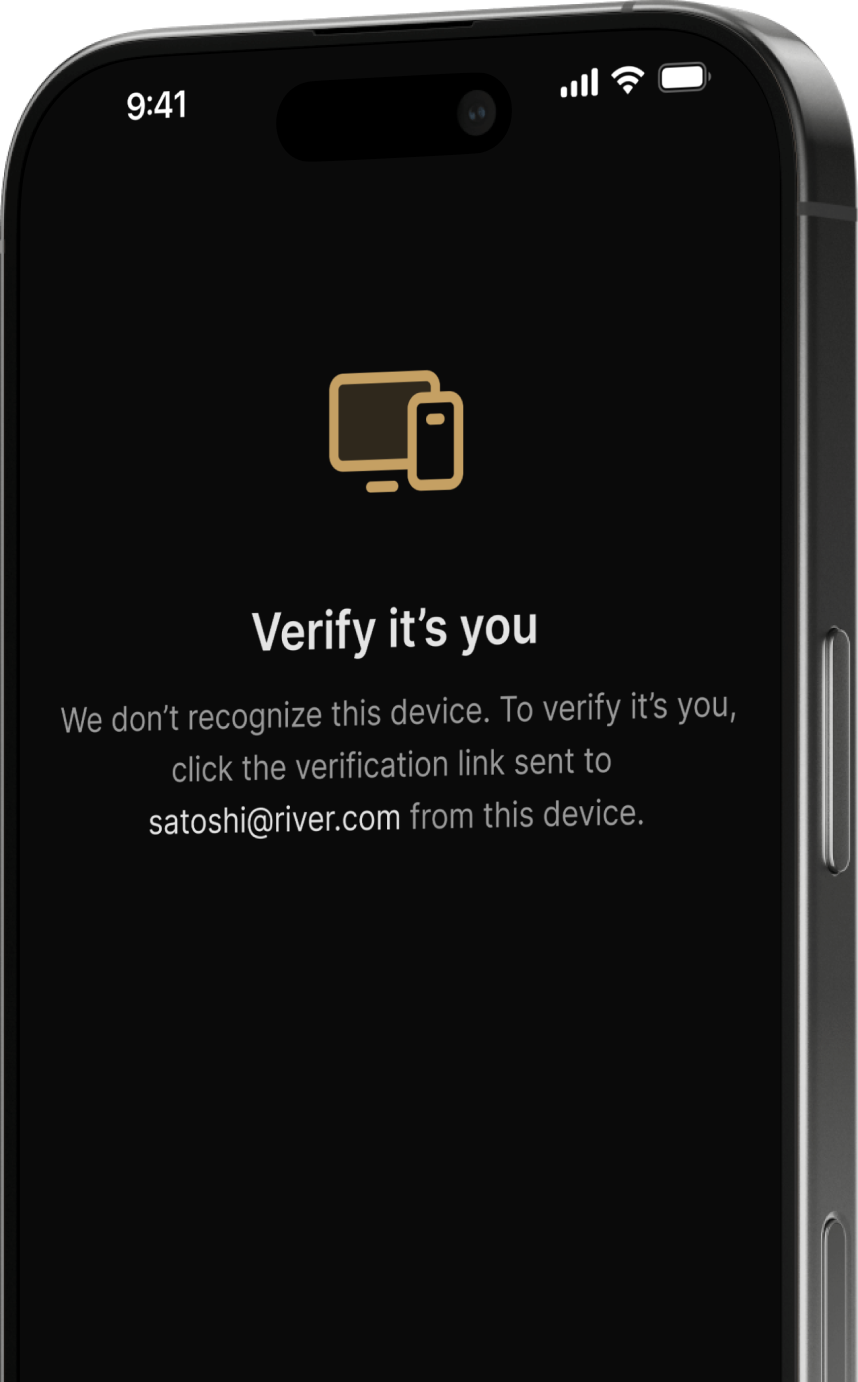
Intelligent account security
We offer security features to help clients protect their funds and personal information.
- 2-factor authentication
- New device verification
- Account notifications
- 24/7 security monitoring
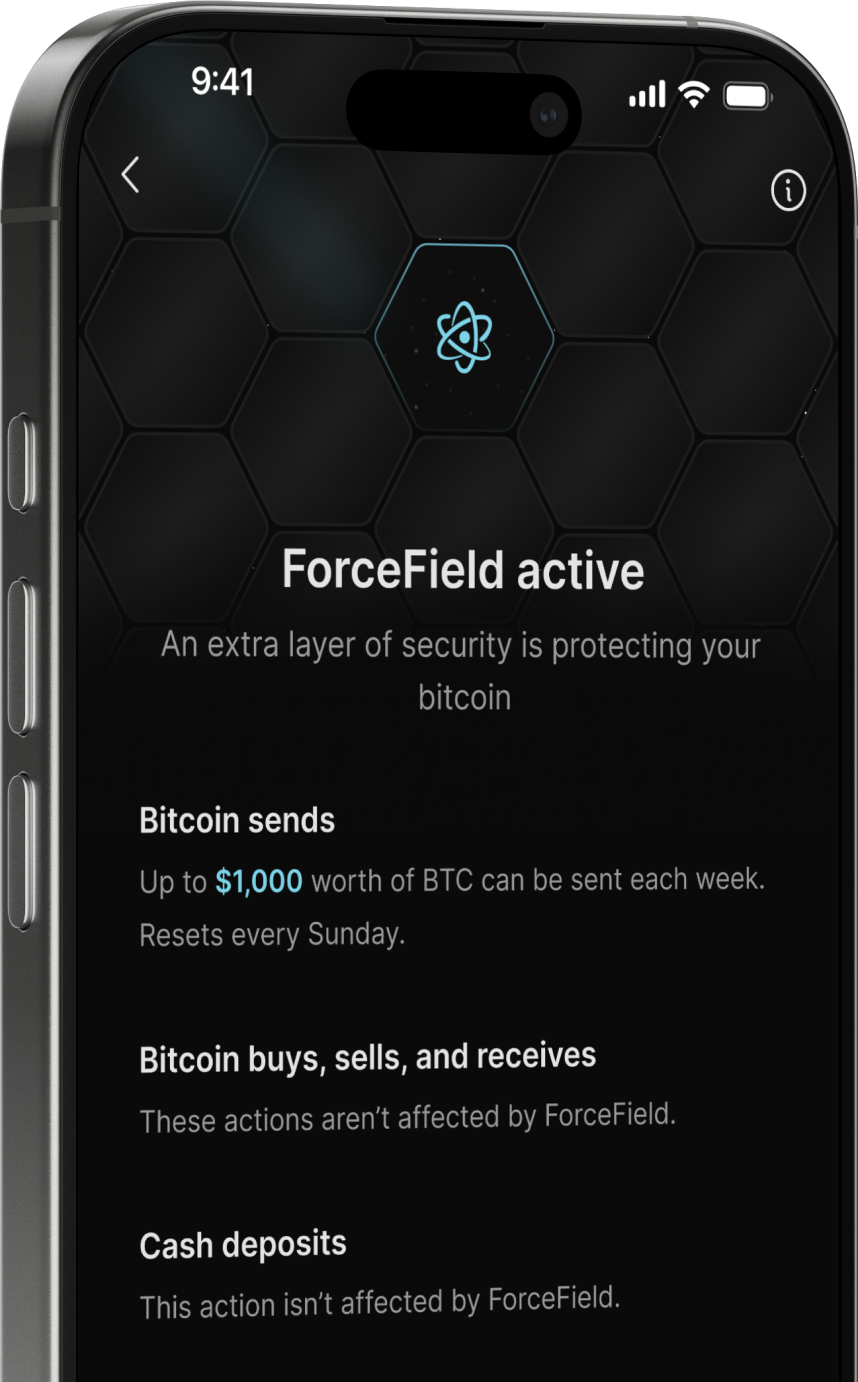
A ForceField for your bitcoin
Add another layer of security to protect your bitcoin in the event of:
- Device theft or loss
- Stolen login credentials
- Scams and phishing attacks
Ask your Bitcoin exchange the hard security questions


Found a security issue you'd like to disclose?

Vulnerability Disclosure Program
We encourage security researchers to partner with us in enhancing River's security. To report a security vulnerability or explore details about our disclosure program, please refer to our security.txt file by clicking the button below.
-
River Financial Inc. (“River”) is not a bank. USD funds are deposited by Lead Bank, Member FDIC. Your USD is FDIC insured up to $250,000, inclusive of any deposits that you already hold at Lead Bank in the same ownership capacity. FDIC Insurance may protect against a failure by Lead Bank, but does not protect against River’s failure, nor does it protect against theft or fraud. Bitcoin is not insured by the FDIC, and may lose value.