Digital Signatures
Bitcoin uses digital signatures to enable coins to be transferred on the blockchain. Digital signatures are used to prove ownership of specific coins and to authorize their transfer to a new owner.
– Satoshi Nakamoto explaining the UTXO model in the Bitcoin Whitepaper (2008)
Currently, Bitcoin uses the Elliptic Curve Digital Signature Algorithm (ECDSA). With the Taproot upgrade, Bitcoin will integrate Schnorr, a second type of signature scheme with several advantages.
➤ Learn more about the Taproot upgrade.
ECDSA
Since Bitcoin’s inception, ECDSA has been used to secure bitcoin. ECDSA was chosen for Bitcoin for a few reasons:
- Open Source. ECDSA was not protected by patents or copyright, so there were no legal issues with using it for Bitcoin.
- Well Tested. ECDSA was widely known and applied when Bitcoin was first designed, and its security was sufficiently established by years of testing.
- OpenSSL. ECDSA was implemented in OpenSSL, an open-source cryptography library used by Bitcoin. This made implementing ECDSA for Bitcoin simpler.
However, ECDSA also has several drawbacks which Schnorr improves upon. For this reason, developers have decided that Bitcoin should implement a different signature scheme, Schnorr.
The Advantages of Schnorr Signatures
Like ECDSA, the Schnorr Digital Signature Scheme uses elliptic curve cryptography (ECC). Schnorr signatures offer several advantages over ECDSA in terms of computational efficiency, storage, and privacy.
Key and Signature Aggregation
The most significant advantage offered by Schnorr signatures is key aggregation. A typical digital signature contains a single public key, a message to be signed, and a signature, asserting that the owner of the public key signed the given message. When multiple parties want to sign the same message, such as spending from a multisig address, they must each include their public key and signature. Thus, if three parties want to sign the same message, the proof will include three public keys and three signatures. This is suboptimal for computation and storage reasons, as each node must perform signature verification, an expensive function, three times and store three sets of signatures and public keys.
Key aggregation eliminates the need for multiple public keys and signatures. Schnorr public keys and signature can be aggregated such that, if three parties want to sign a transaction, they can trustlessly combine their three public keys to form a single public key. Then, using each of their three private keys, they can sign the same message. Finally, they can combine their three signatures to form a single signature which is valid for the aggregate public key. A verifier must only verify a single signature and public key in order to be sure that all three parties signed the message.
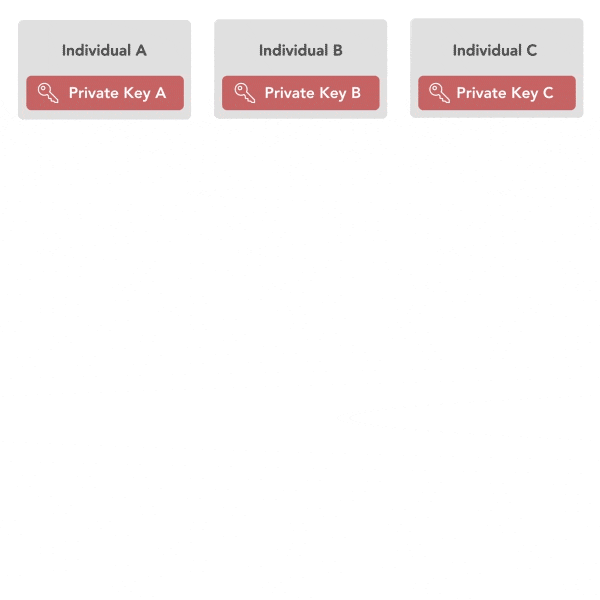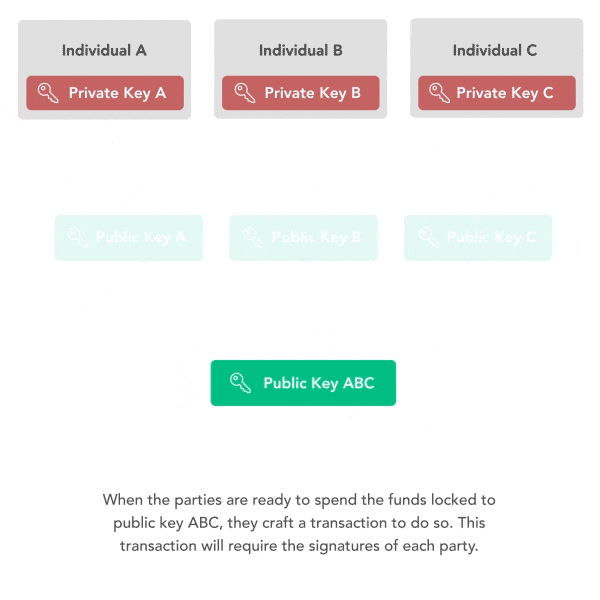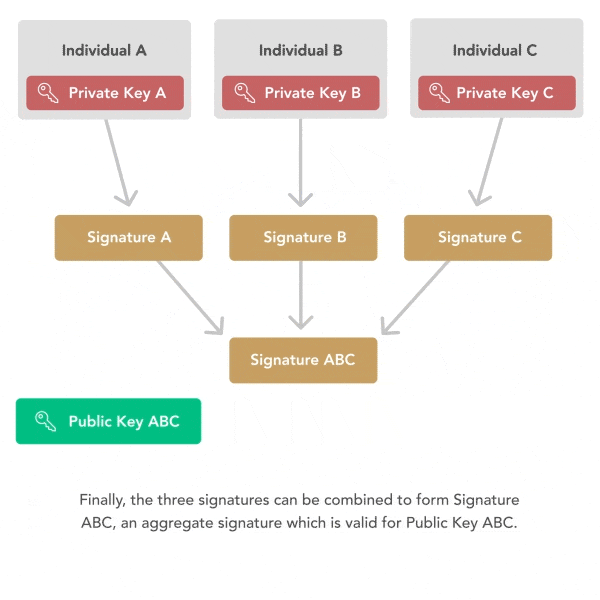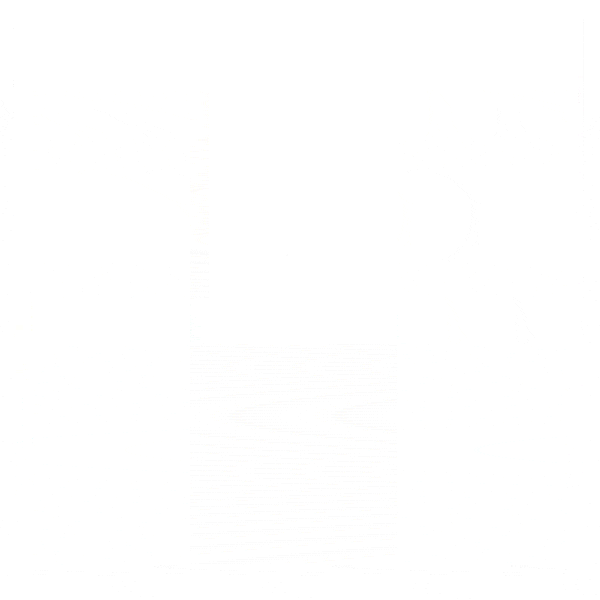
The privacy implications of key aggregation are significant. Because multiple parties can aggregate keys and signatures, multisig transactions can perfectly resemble singlesig transactions. Thus, all Schnorr spends will resemble each other, making it impossible for chain analysis to differentiate between multisig spends and single signature spends. This will invalidate several heuristics used by chain analysis, including the common input ownership heuristic and the script type heuristic. This privacy benefit will extend to all Bitcoin users who use Schnorr, but not to those who use ECDSA transaction types.
Batch Verification
When a node receives a new block, it normally verifies every transaction and signature in that block one by one. This is a time consuming and resource intensive process.
Key aggregation allows Bitcoin nodes to verify signatures in batches. This method significantly reduces the time and compute power required to verify a transaction with many inputs.
Why Did Bitcoin Not Use Schnorr Earlier?
Schnorr Signatures have been protected by patent since their invention in 1990, heavily restricting their use and stifling innovation. Since ECDSA was open source, it was widely utilized, rigorously tested, and trustworthy. Although the Schnorr patent expired in 2008, the same year Bitcoin was invented, it was decided that Schnorr signatures lacked the popularity and testing required to secure a system as critical as Bitcoin.
Schnorr signatures will be introduced to Bitcoin through Taproot upgrade, which will hopefully be activated around 2022. Although developers have added all necessary code to Bitcoin Core, Bitcoin nodes must accept the upgrade in order to consider Schnorr signatures valid.
Key Takeaways
- Digital signatures are used to move bitcoin on the blockchain. Bitcoin has previously used ECDSA as the digital signature algorithm to do so.
- In the near future, Bitcoin will enable Schnorr signatures in addition to ECDSA signatures. Schnorr signatures present multiple advantages over ECDSA.
- Schnorr will improve privacy for all Bitcoin users. Schnorr will also realize fee savings for those using Schnorr and Taproot.


